1. What do you think about cloud computing? Please give your own definition of cloud
computing.
2. Please describe the features of big data.
3. Please describe the relations between big data and cloud computing.
4. Please compare the HTC and HPC, and give an example for each of them.
5. Discuss the on-demand computing's advantages over traditional computing.
6. Please discuss the seven characteristics of cloud computing.
7. Please describe the virtualization of cloud computing.
1. Please describe the system architecture of cloud computing, including the four layers and
two domains.
2. Please describe the functions of cloud components in the platform layer.
3. Please the main functions performed in the management domain.
4. Please give examples to IAAS, PAAS, DAAS and SAAS.
5. Please describe the difference between public cloud and private cloud.
6. Please discuss why need the hybrid cloud, and how to implement it.
7. Please discuss the challenges of cloud computing.
1. What is a computing cluster?
2. Please describe the architecture of a computing cluster.
3. Please analyze the top 500 supercomputers and their features including architectural
evolution, performance and detailed machines
4. Please tell the difference between availability and reliability, and give the equations
to compute them.
5. Please explain how the Single System Image (SSI) works for clusters.
6. Please discuss the challenges for single entry point as described in the following
picture.
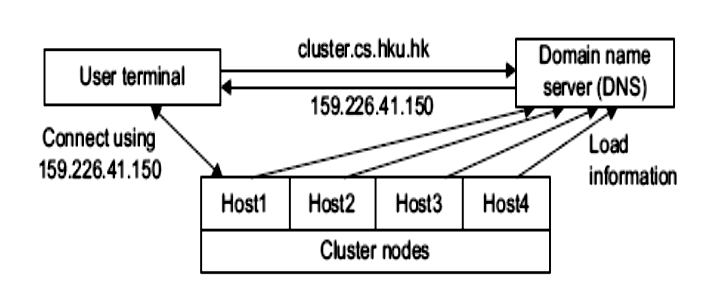
1. What is virtualization in a computer system?
2. Please describe the virtualization of five abstraction layers.
3. Please analyze the “one to multiple", "multiple to one", and "multiple to multiple"
virtualization.
4. Please tell the difference between the following two virtualizations:
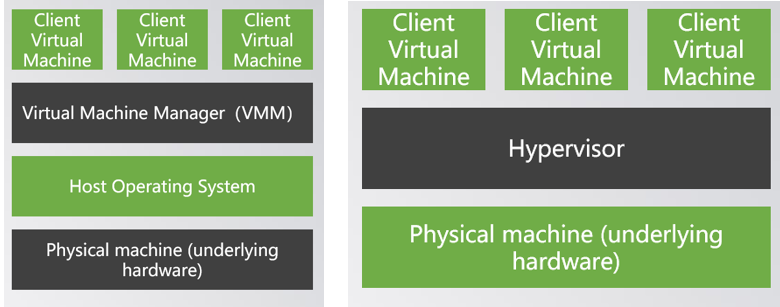
5. Please explain the difference between full virtualization and paravirtualization.
6. Please discuss the address transform in memory virtualization
7. Please describe the procedures of virtual machine migration
8. Please tell us how to combine the different approaches in the following to achieve
virtual machine migration
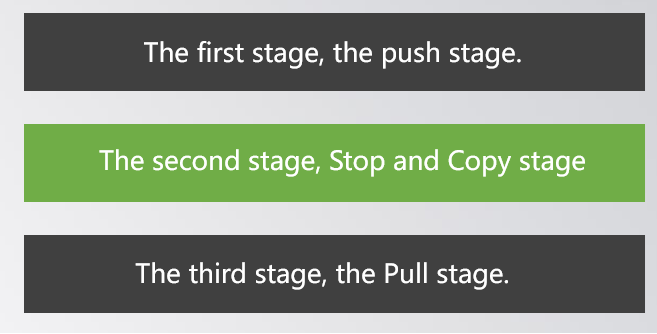
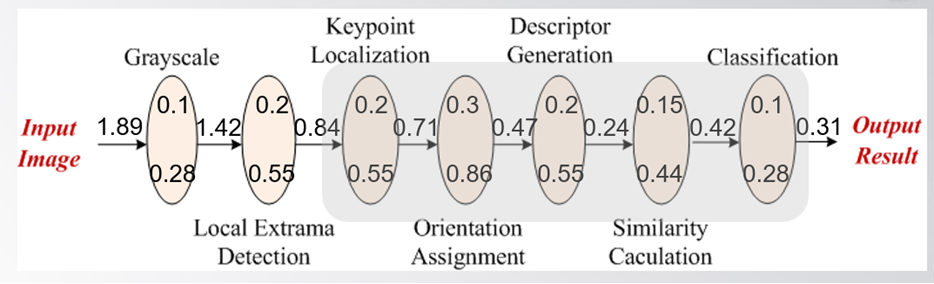
1. What is computation partitioning and its motivation in cloud computing?
2. Based on the following picture to illustrate the divide and conquer idea used in cloud
computing.
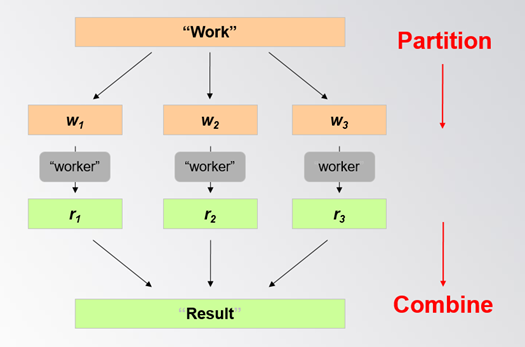
3. Please discuss why not just all the computing in the server side or in the client
side?
4. Analyze in the following setting, whether more than twice transmission between the server
and the client side will make better result?
5. Please write codes for the optimal partitioning problem and generate another data set to
test your codes
6. Please discuss how to handle the relations among components in the computing diagram?
1. What parallelization problems will we encounter in the cloud computing systems?
2. Please describe the differences between deadlock and livelock.
3. Please discuss how mapReduce helps the developer to simplify the application design.
4. Please compute the result with the following Lisp function:
(fold + 5 '(1 2 3 4 5))
5. Discuss how does the shuffle and sort intermediate results implement in the mapReduce.
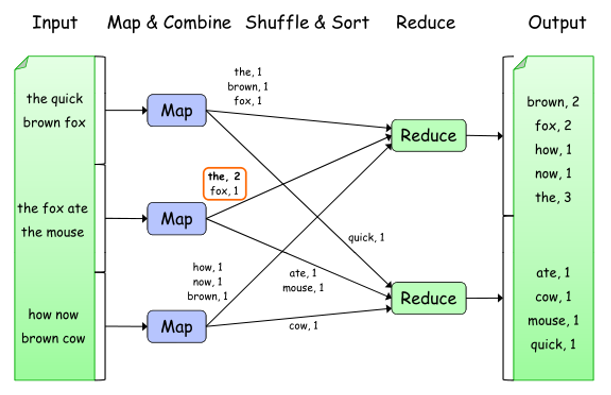
6. Please write the pseudo codes of mapReduce for word counting

7. Please improve the above codes when we want to find the popular ten words.
8. Write the codes for word sorting using mapReduce.
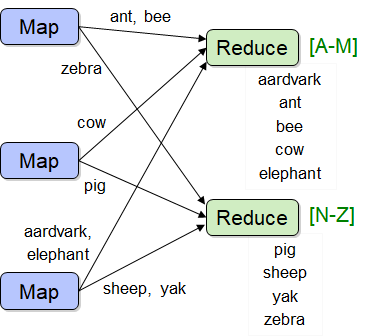
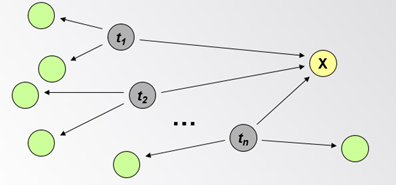
9. How to implement the PageRank using mapReduce in clouds?
Given page x with in-bound links t1…tn, where C(t) is the out-degree of t, α is
probability of random jump, and N is the total number of nodes in the graph, we have
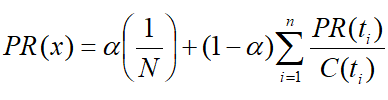
1. What is distributed file systems?
2. Why we needed HDFS in mapReduce? What are the main components in a HDFS system.
3. Discuss the fault tolerance in mapReduce when tasks or nodes crash.
4. What is the straggler, and how to handle the straggler.
5. In the following application, please write the codes using combiner.
6. Please write codes for numerical integration using mapReduce.
7. Using both pairs and stripes to write the codes for conditional probabilities.
1. What is service-oriented architecture (SOA)?
2. Please describe the REST architectural style principles.
3. Please based the following picture to show how a web service works.
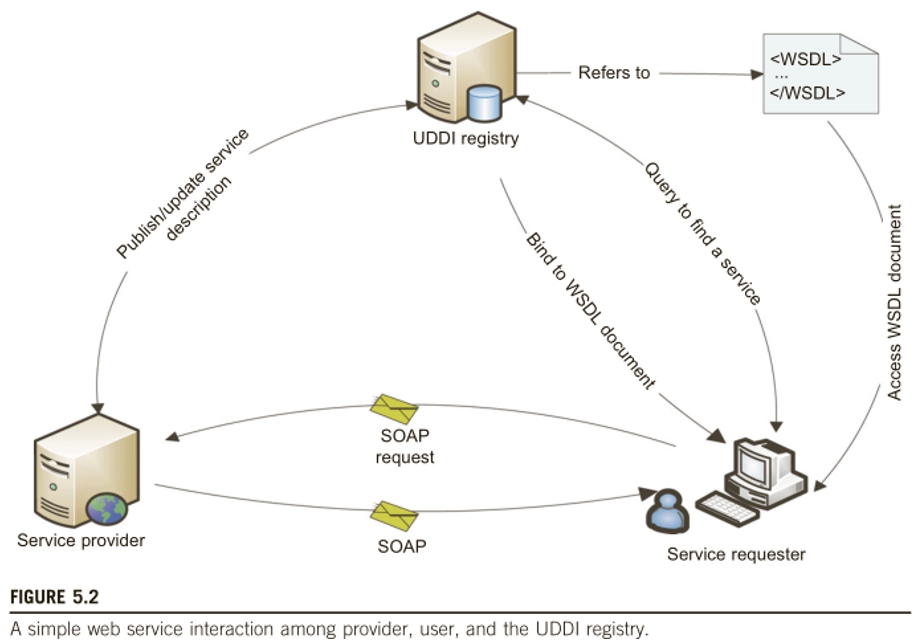
4. Please provide three examples of web services.
5. Please describe the WS-I protocol stack.
6. Please discuss the objectives of UDDI and service registries.
7. Please give an example to use workflow in service-oriented architecture.
1. What problem does the Paxos algorithm solve?
2. How does the Paxos algorithm ensure data consistency?
3. What problem does the DHT algorithm solve?
4. Please provide examples of which distributed systems currently use the DHT
protocol.
5. Based on the following picture, please describe how DHT find the key 54, and key 38?
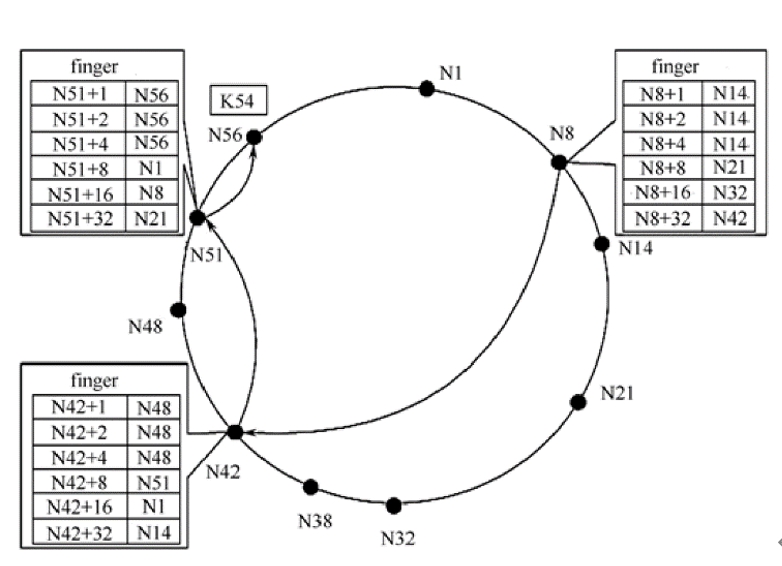
6. In the traditional network protocol hierarchy, where is DHT located?
7. What problem does the Gossip protocol solve?
8. What are the three ways of message propagation in the Gossip protocol?
9. Please draw a schematic diagram of message propagation in the CoolStreaming system.
1. Please describe the relations between Cloud Computing and IOT.
2. Please describe the opportunities of IOT in 3 dimensions.
3. Please describe the main components in an RFID system based on the following picture.
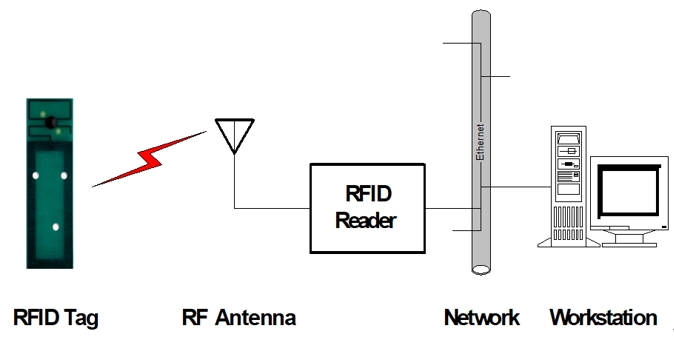
4. Please describe three applications of RFID.
5. Please describe the ALOHA approach for solving tag collisions
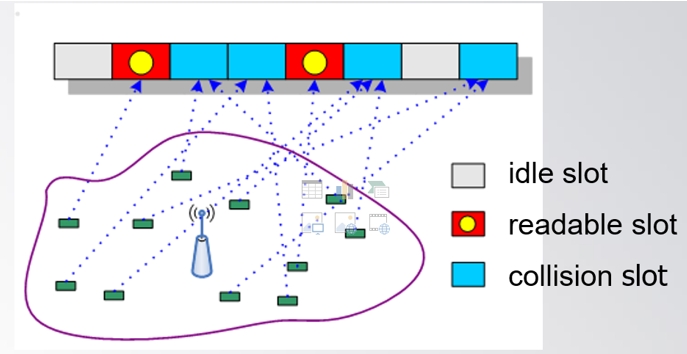
6. Please describe how do sensors form a wireless sensor network.
7. Please describe a typical application of WSN.
8. How does a real-time GPS tracking system work?
9. Please discuss how cloud support the Internet of Things.
1. What opportunities does the development of cloud computing bring to the security field?
Please provide examples to illustrate.
2. Attempt to compare the similarities and differences between traditional information
security and cloud security from the perspective of different service models in cloud
computing.
3. Compare the differences in cloud security requirements under different service models.
4. Please describe what problem does the following picture shows in the cloud security.
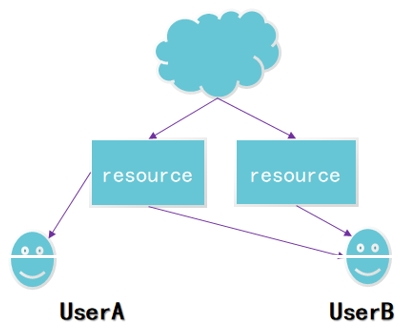
5. What technologies should be used to prevent the virtualization security threats?
6. Research and point out the usage scenarios of homomorphic encryption algorithms in cloud
based secure data storage and computing.
7. Explain the security as a service in cloud computing and provide several examples of
security as a service to illustrate which advantages of cloud computing are utilized.
8. Summarize the commonalities among various cloud computing security standards and explain
the necessity of these commonalities.
